As Sesame Street moves to Netflix, we might be reminded that cookies are often ravenously delicious even if you’re left counting the empty calories.
Web users might be familiar with a different kind of cookie, signified less like a tasty snack and more an annoying pop-up. Non-Californian American browsers might be less susceptible to this kind of nonsense, but European users have – in the name of “privacy” – been compelled to deal with prompts before they can see a site they’ve clicked on. Like just about any T&Cs or software licensing EULAs, most people just want to get rid of the prompt as quickly as possible so might be drawn to the most-prominent “Accept” button.
It can be pretty eye-opening if you do pay attention – many sites potentially share the way you browse with thousands of third parties. Dive into the more advanced settings on each of the se prompts and you might be able to enable and disable individual “partners” or tweak exactly which kind of information is being tracked. But who’s got time for that?
Mmmmm. Cookies.
Back in the mid 1990s, when the web was taking shape, telecoms company MCI was developing an early e-commerce application with Netscape, but didn’t want their web server to have to track every stage of incomplete transactions. So, the developers took an idea that had been previously used, called a “magic cookie”, as a way of temporarily storing a block of data on the user’s computer. Thus, the HTTP Cookie, aka web cookie and so on, became a standard in 1997.
In general, cookies are supposed to make browsing the web more seamless – when you go to a website, a cookie from a previous visit could be used to continue a previous process or remember some preference you had – like how many items you want in a list or how to sort it – without needing to log in.
But cookies give website developers a raft of ways to silently track users, while also opening the door to all kinds of nefarious behaviours either on behalf of the site owners or unknown 3rd party players.
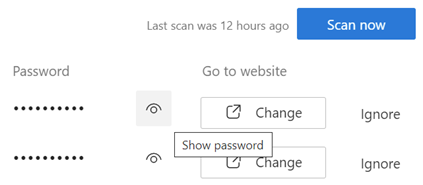
Look in your browser settings and you’ll see various ways where you can control the usage of cookies, and see what sites have put on your machine…
Visiting a single site, you can see what cookies are in use, and individually inspect, disable or delete them.
Using addins to stop foul play
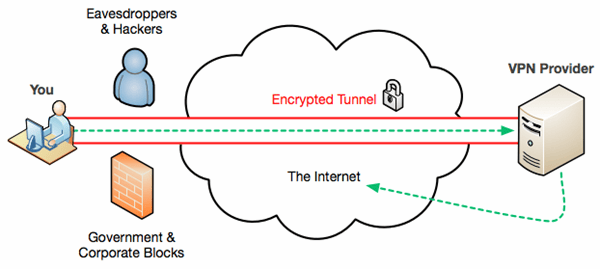
Even if you are a trusting soul, it makes sense to use some common addins to limit what 3rd parties can see and know about you while browsing the web. Popular tools that might reduce tracking, cookies and block ads include Privacy Badger, I Don’t Care About Cookies, uBlock Origin and many more.
Most of these kind of tools will give you the option to “whitelist” a website, in case turning off all its tracking and cookies actually breaks the site, so there’s little risk in using the well-known ones. Be very careful of any unsolicited add-ons trying to install themselves via popups or any other means.
Check out the EFF’s “Cover Your Tracks” page as well – it gives you a report on how well tied down (through addins or configuration) your browser really is.
Should you Accept, or Reject All?
Most of the time, the options are straightforward, even if the Accept button is more prominent; many sites will let you Reject cookies and will still work more-or-less intact. There are both temporary cookies that only live as long as your session, and persistent ones which stay on your computer so you can be identified next time you show up. There are a few different types typically used:
· Functional – these are used to track things like your basic preferences on the site, what country you are in and so on. There should be nothing to fear here but if you use an addin or a browser setting to completely block cookies, the site might just not work.
· Performance or analytical – these track how you use the website, and are generally anonymised so just provide the site owner with a way of improving their service.
· Advertising – usually a mix of 3rd party sites which track what you do, across different sites. That’s why if you’re shopping for something one minute, you start to see adverts for the same kind of thing on different websites. Do you want to have your browsing patterns exposed to potentially thousands of advertisers so they can foist more stuff at you?
You could try disabling third-party cookies as one way of avoiding advert spam.
In Google Chrome:
In Microsoft Edge:
There is a school of thought which says you’d be better off rejecting as much as you can when asked for what to allow, in conjunction with anti-tracking and ad-blocking addins. Some sites will still make you jump through multiple hoops to individually disable lots of options to effectively “Reject All”.
Some sites just won’t let you get by without either Accepting everything or by paying for a subscription; your choices then are to accept their meddling oversight, pay their toll, or just don’t look at their pages.









![clip_image002[4] Quick Assist logo](/wp-content/uploads/2022/06/clip_image0024_thumb.gif)
![clip_image004[4] Quick Assist update](/wp-content/uploads/2022/06/clip_image0044_thumb.gif)
![clip_image006[4] Sharing security code](/wp-content/uploads/2022/06/clip_image0064_thumb.gif)
![clip_image002[6] clip_image002[6]](/wp-content/uploads/2022/06/clip_image0026_thumb.gif)