Childhood games sometimes revolved around the goodies and the baddies. Early Western movies often had the convention of good guys wearing white hats and villans wearing black; if nothing else, it helped the viewer distinguish who was who in a fast-moving fight scene when the film is shot in monochrome.
Childhood games sometimes revolved around the goodies and the baddies. Early Western movies often had the convention of good guys wearing white hats and villans wearing black; if nothing else, it helped the viewer distinguish who was who in a fast-moving fight scene when the film is shot in monochrome.
White hat and Black hat are also terms given to computer hackers, the black hats being figuratively worn by criminals trying to break in to systems for nefarious gain, whereas the white hat hackers do it so they can report vulnerabilities and make things more secure. As ever with computing, there are also many shades of grey.
In your own technology environment, you probably never see the bad actors until you are dealing with the aftermath of a security breach. Check that your common usernames and passwords are not being circulated around, by using the Password Monitor in Edge and look for known leaks at Have I Been Pwned.
If you use a Microsoft Account (also known as MSA, commonly identified with domains like outlook.com, hotmail.com, live.com etc), then it’s a good idea to make sure it has a complex password and most importantly that muti-factor authentication is enabled. See best practices for managing your MSA.
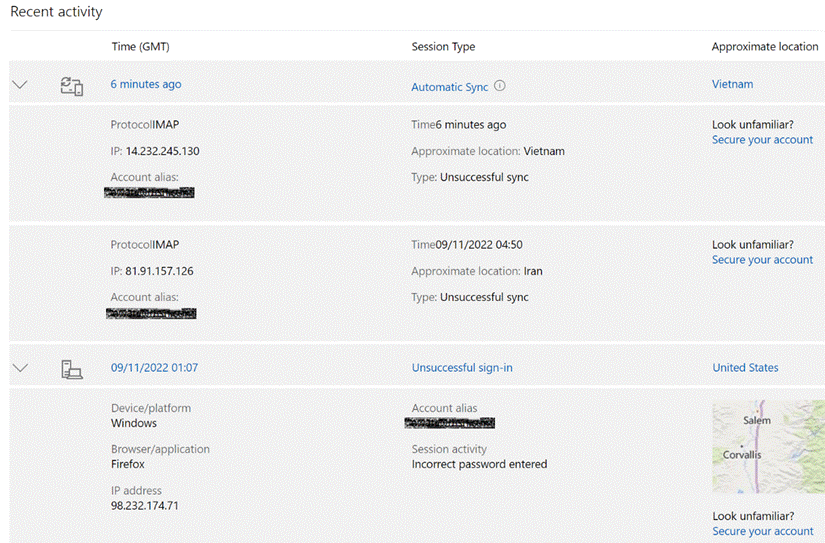 If you’d like to scare yourself, take a look at the activity history for your MSA – here – and you’ll probably see lots of attempts to sign in from places you’ve never been to, if it was even possible to have visited them in the timeframe of the activities.
If you’d like to scare yourself, take a look at the activity history for your MSA – here – and you’ll probably see lots of attempts to sign in from places you’ve never been to, if it was even possible to have visited them in the timeframe of the activities.
Hopefully all the unrecognized tries to sign in have been denied… maybe it’s a good time to log in to any old Hotmail.com etc accounts you may still have, just to make sure they are secured appropriately?
It used to be considered a good idea to change passwords regularly, but in recent years that has been discouraged. It would be safer to have a long, complex password which is unique for each website or account you use, probably hooked up with a password manager and authenticator app. You could even remove the password altogether and use only multi-factor authentication.
MFA – or 2FA – isn’t perfect, though. El Reg reports on a very real threat to enterprise security, described as “MFA Fatigue” – when an administrator of a system who normally has to use MFA to access it, is bombarded by authentication prompts at times they don’t expect.
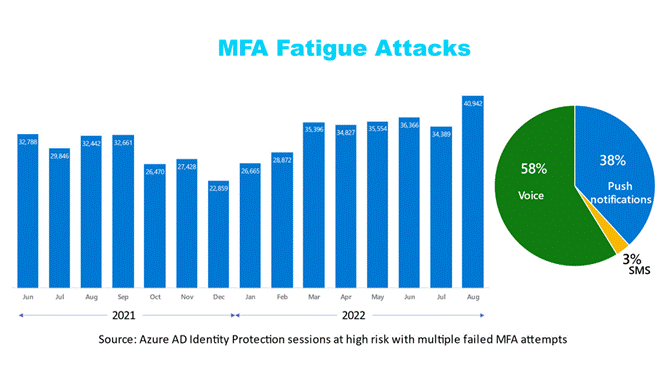 Human nature might assume the system is playing up, and eventually hit “Approve” on the MFA screen, to stop the annoyance.
Human nature might assume the system is playing up, and eventually hit “Approve” on the MFA screen, to stop the annoyance.
Microsoft’s security prouct group has some advice on how to protect users from MFA Fatigue Attacks and has released a bunch of updates to the Microsoft Authenticator app and the back-end services to hopefully make it less of a threat.
The primary problem with all IT security though, ultimately sits between the keyboard and the chair.